default-encrypt-method-sha512
Installation
cfbs add default-encrypt-method-sha512
MD5, DES, and other older hashing algorithms are no longer secure, and shouldn't be used for any cryptographic purposes. A good first step towards enforcing stronger cryptography is to set the default password hashing algorithm to SHA-512.
This module makes sure the default password hashing algorithm is SHA512.
Yes, it's a bit of a mis-nomer, but that stems from the historical details, namely the key ENCRYPT_METHOD in /etc/login.defs.
Recommendation: Don't use MD5 or other insecure hashing algorithms. Use this module to enforce a strong default across your systems. Look into what other places you might be relying on outdated cryptographic algorithms and how you can eliminate them. (See for example FIPS mode).
Examples
Running CFEngine with this module in your policy set on a system which uses MD5 looks like this:
$ cat /etc/login.defs | grep '^ENCRYPT_METHOD'
ENCRYPT_METHOD MD5
$ cf-agent -KI
info: Replaced pattern '^\s*(ENCRYPT_METHOD\s+(?!SHA512$).*|ENCRYPT_METHOD)$' in '/etc/login.defs'
info: replace_patterns promise '^\s*(ENCRYPT_METHOD\s+(?!SHA512$).*|ENCRYPT_METHOD)$' repaired
info: Edited file '/etc/login.defs'
$ cat /etc/login.defs | grep '^ENCRYPT_METHOD'
ENCRYPT_METHOD SHA512
If you run cf-agent -KI again, the file will already be correct, no changes will be made and there will be no log messages.
Of course, you don't have to run the policy manually from the command line.
As long as the module is included in your policy set and deployed to your policy server, it will be automatically enforced in all your infrastructure.
This module does not provide an inventory attribute for ENCRYPT_METHOD, but you can get that in the inventory-etc-login-defs module.
Even so, CFEngine Enterprise reports the outcomes of everything it does, so you can always verify that the correct value is set.
You can navigate to the policy file and line number in Policy Analyzer within Mission Portal, the CFEngine Enterprise UI:
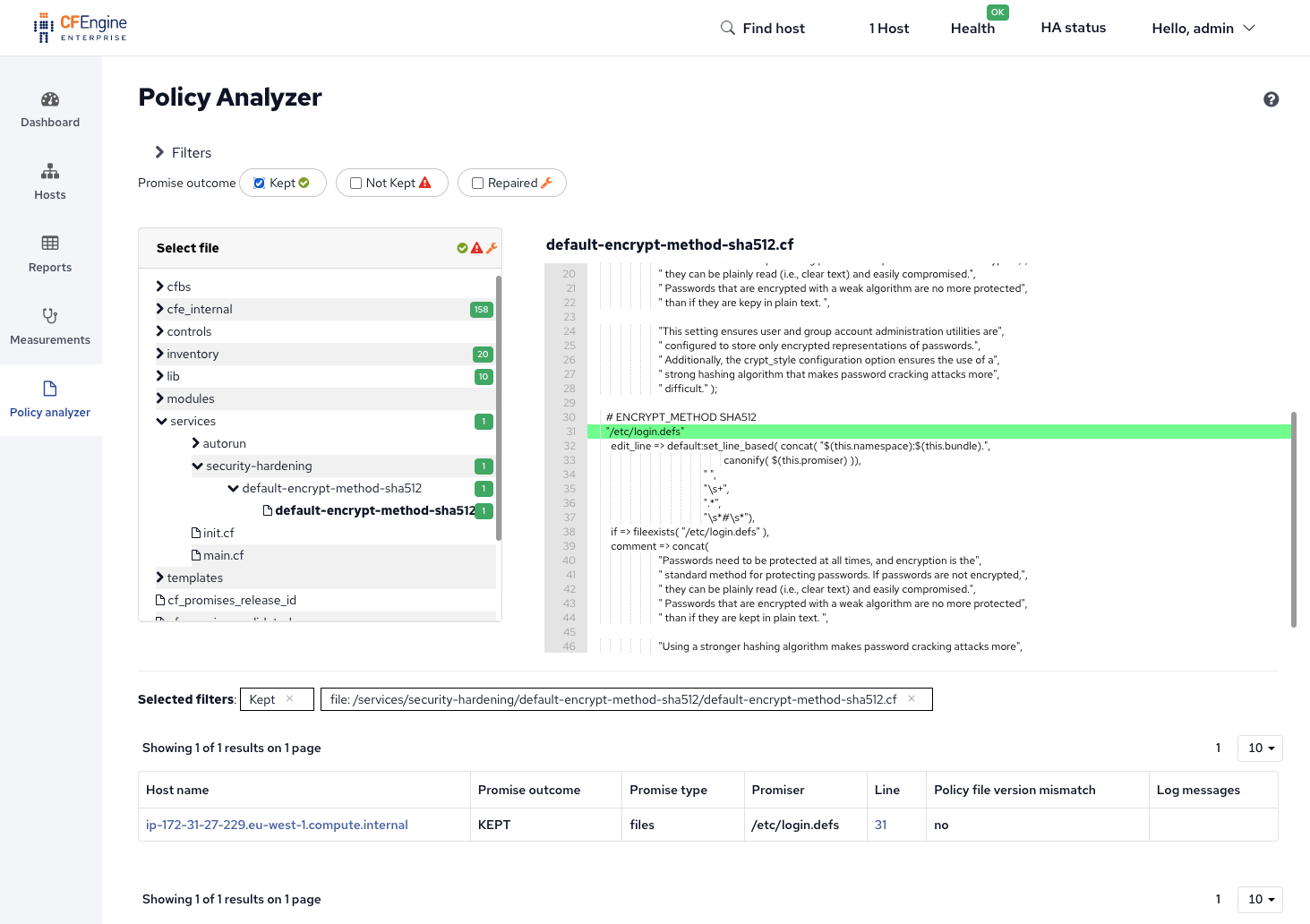
Above we see that the promise to edit /etc/login.defs was KEPT.
This means that the file was already correct, the hashing algorithm was set as ENCRYPT_METHOD SHA512, and no edit was necessary.
How it works
Specifically, this module does 2 things:
-
Enforce Password Hashing Algorithm in
/etc/libuser.conf(SHA512)crypt_style = sha512
-
Enforce Password Hashing Algorithm in
/etc/login.defs(SHA512)ENCRYPT_METHOD SHA512
Note
This policy only ensures the default algorithm is set, it does nothing with respect to users who have passwords hashed using a different algorithm.
Related modules:
Dependencies
This module has no dependencies