delete-files
Installation
cfbs add delete-files@1.0.0
A simple module to delete specific files.
It allows you to specify a list of files you want deleted on hosts in your infrastructure. When this module is deployed as part of your policy set, every time CFEngine runs, it will check if those files exist, and delete them if they do.
Recommendation: Enforce the removal of files known to be malicious or indicating insecure configuration. Examples of such files are `~/.shosts` files, `/etc/cron.deny`, etc.
Configuration
Module input
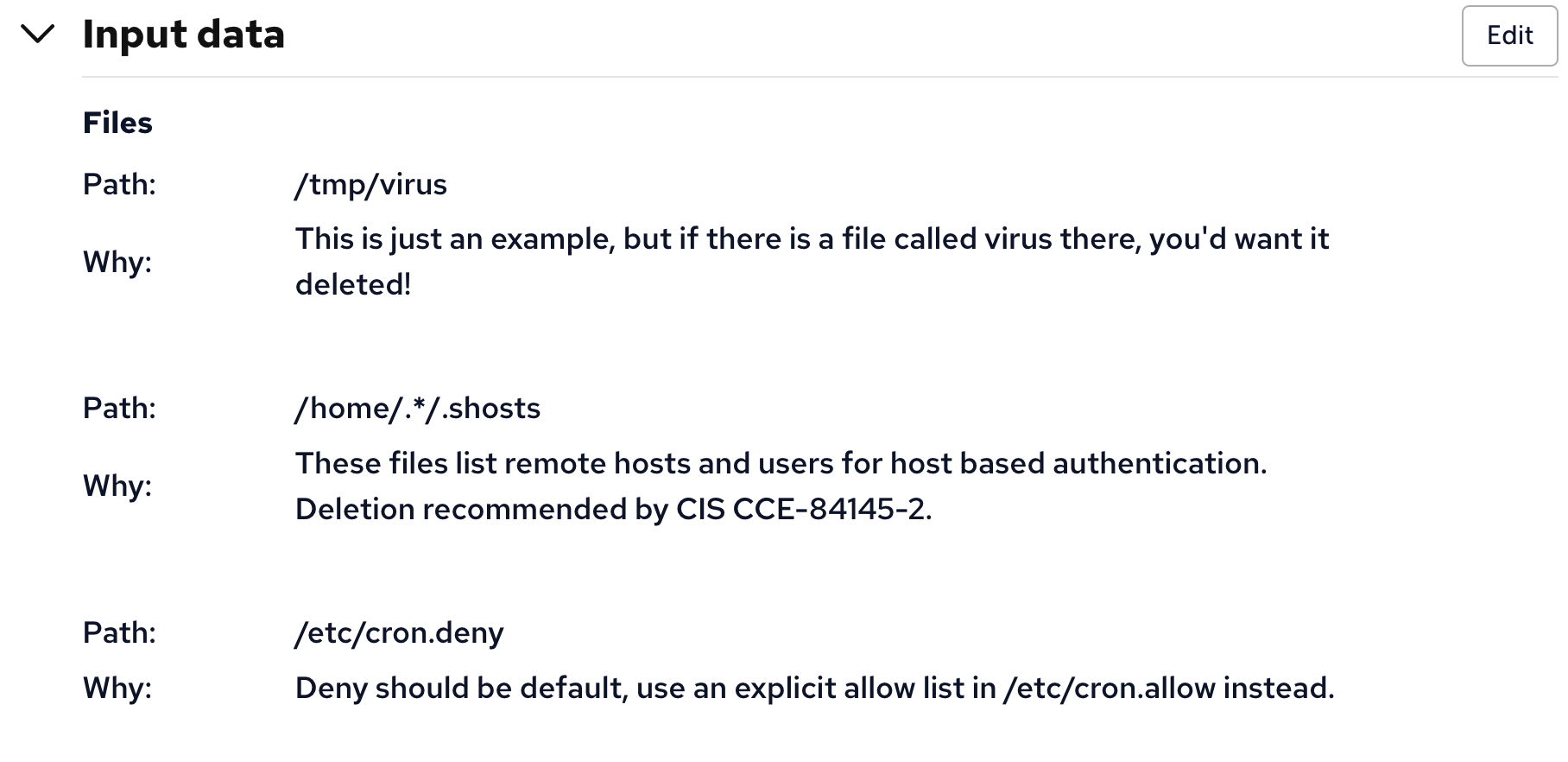
This module accepts input. Both the cfbs CLI and Mission Portal (3.21 and beyond) allow you to specify the files you want deleted. Here is an example of what it looks like in Mission Portal:
Variables
-
delete_files:delete_files.files -
Array of dicts having
pathandwhykeys.pathmust be a regular expression matching the fully qualified path to a filewhyshould explain why the file being absent is important
{
"variables": {
"delete_files:delete_files.files": {
"value": [
{
"path": "/tmp/virus",
"why": "This is just an example, but if there is a file called virus there, you'd want it deleted!"
},
{
"path": "/home/.*/.shosts",
"why": "These files list remote hosts and users for host based authentication. Deletion recommended by CIS CCE-84145-2."
},
{
"path": "/etc/cron.deny",
"why": "Deny should be default, use an explicit allow list in /etc/cron.allow instead."
}
],
"comment": "Files and their required permissions"
}
}
}Testing that it works
After adding the file paths you want deleted (via input or JSON) you can touch the files and see that they get deleted:
$ sudo touch /tmp/virus /home/ubuntu/.shosts /etc/cron.deny && sudo cf-agent -KI
info: Deleted file '/tmp/virus'
info: Deleted file '/home/ubuntu/.shosts'
info: Deleted file '/etc/cron.deny'
Dependencies
This module has no dependencies