enable-aslr
Installation
cfbs add enable-aslr
Address space layout randomization (ASLR) helps prevent exploits by randomly changing the address at which programs are located. Without ASLR an exploit can rely on the location of various aspects of a program and more easily perform an attack. This feature was first introduced around 2005 in Linux and subsequently in most other operating systems in the following years. 64-bit systems benefit more from this feature because the larger address space allows for greater entropy in randomizing the locations of programs. At this time there are known exploitations even of this protection mechanism but it is still best practice to ensure this feature is fully enabled on your systems.
Recommendation: Ensure that ASLR is fully enabled on all systems to make exploits relying on address space layout more difficult.
Inventory
After adding this module you can view which hosts have ASLR enabled in Mission Portal Inventory Report:
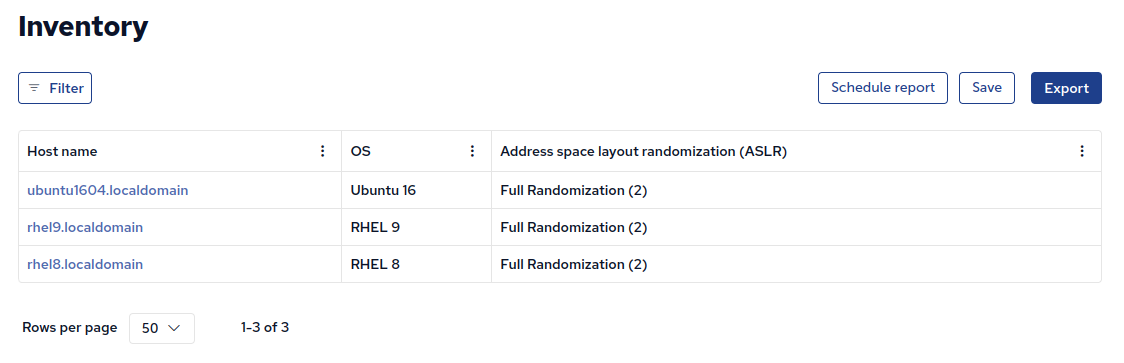
Example
On a linux system with ASLR disabled an agent run will enable it permanently by adding /etc/sysctl.d/60-enable-aslr.conf. The policy will run sysctl --system to apply the change.
$ sudo sysctl -w kernel.randomize_va_space=0
$ cf-agent -KI
info: Created file '/etc/sysctl.d/60-enable-aslr.conf', mode 0600
info: Updated file '/etc/sysctl.d/60-enable-aslr.conf' with content 'kernel.randomize_va_space = 2'
info: Executing 'no timeout' ... 'sysctl --load /etc/sysctl.d/60-enable-aslr.conf'
notice: Q: "...sysctl --load /": kernel.randomize_va_space = 2
info: Last 1 quoted lines were generated by promiser 'sysctl --load /etc/sysctl.d/60-enable-aslr.conf'
info: Completed execution of 'sysctl --load /etc/sysctl.d/60-enable-aslr.conf'
Adding exceptions
If ASLR cannot be enabled for some reason, you can add an exception with the exception_enable_aslr class.
This class can be set within def.json (Augments), from policy, or in the Host specific data section in host info pages inside Mission Portal, the CFEngine Enterprise Web UI.
Dependencies
This module has no dependencies