lynis
Installation
cfbs add lynis
Lynis is a security tool for hosts running Linux, macOS, or other Unix-based operating systems. It performs an extensive health scan of your host to support system hardening and compliance testing.
This module provides policy to automate the installation, running, and reporting of CISOfy's lynis system audits finding.
Configuration
Variables
-
lynis:globals.version - The version of Lynis desired to be installed. (default
3.1.3) -
lynis:globals.archive_hash - The hash of the archive that Lynis is to be installed from (used for integrity checking). (default
bb51569c8f9e67bd2d2aa5cfcdd8e2d82726552b69fde4abddff9d991706f554) -
lynis:globals.hash_type - The type of hash to verify the downloaded archive with.
-
lynis:globals.tar_url - The http/https url from which to download the archive. Note that the filename should follow the default pattern (
lynis-$(version).tar.gz).
Note: Configuring these variables via Augments requires the use of the variables key (introduced in CFEngine 3.18.0). These variables are also configurable via module input.
{
"variables": {
"lynis:globals.version": {
"value": "3.0.8",
"comment": "The version of Lynis desired."
},
"lynis:globals.archive_hash": {
"value": "98373a4cc9d0471ab9bebb249e442fcf94b6bf6d4e9c6fc0b22bca1506646c63",
"comment": "The hash (sha256) listed for the tarball hosted on the Lynis website (https://cisofy.com/downloads/lynis/)."
}
}
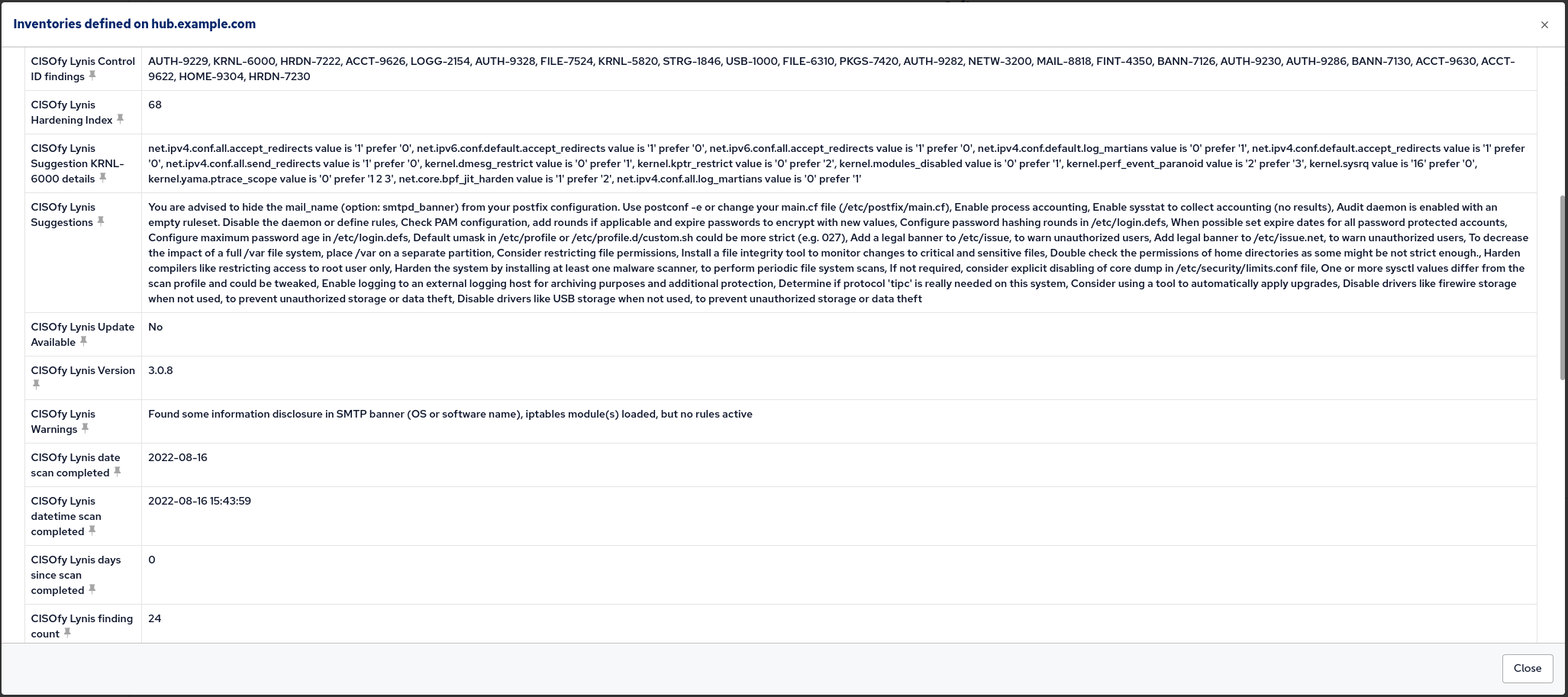
}Inventory
- CISOfy Lynis Version
- The version of Lynis installed
- CISOfy Lynis Suggestions
- A list of suggestions from the last scan report.
- CISOfy Lynis Warnings
- A list of warnings from the last scan report
- CISOfy Lynis Control ID findings
- A list of the Lynis Control IDs surfaced as warnings or suggestions.
- CISOfy Lynis finding count
- The number of findings resulting from a scan.
- CISOfy Lynis datetime scan completed
- Datetime of last completed scan.
- CISOfy Lynis date scan completed
- Date of last completed scan (YYYY-MM-DD).
- CISOfy Lynis days since scan completed
- Days since Lynis scan last completed.
- CISOfy Lynis Hardening Index
- Hardening index from last scan.
- CISOfy Lynis Update Available
- Whether or not there is an updated version of Lynis available.
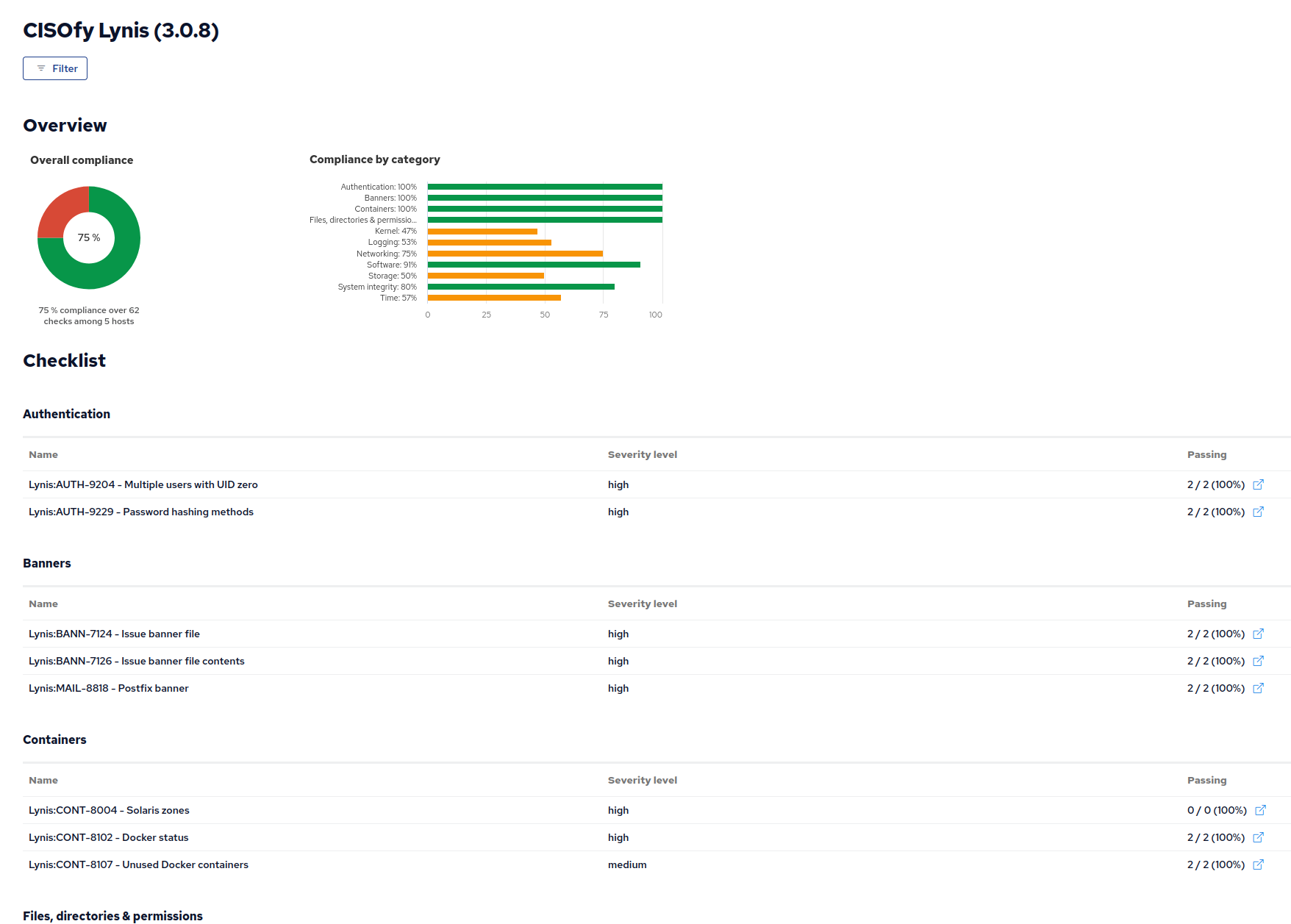
Compliance Report
Tools and example compliance reports for use with CFEngine Enterprise can be found under ./compliance./compliance-reports/.
Usage
Forcing report re-generation
When the class lynis:want_report_generated_now is defined Lynis will be run and lynis-report.dat will be updated.
[root@hub lynis]# cf-agent -KI --define lynis:want_report_generated_now
info: Executing 'no timeout' ... '/opt/lynis/lynis-3.0.7/lynis audit system --quiet --auditor 'CFEngine cf-agent''
notice: Q: "....0.7/lynis audi": /opt/lynis/lynis-3.0.7/include/tests_mac_frameworks: line 161: permissive: command not found
Q: "....0.7/lynis audi": /opt/lynis/lynis-3.0.7/include/tests_mac_frameworks: line 162: permissive: command not found
info: Last 2 quoted lines were generated by promiser '/opt/lynis/lynis-3.0.7/lynis audit system --quiet --auditor 'CFEngine cf-agent''
info: Completed execution of '/opt/lynis/lynis-3.0.7/lynis audit system --quiet --auditor 'CFEngine cf-agent''
–info level output
If used from the command line, you can add the --info option to see all the results from Lynis:
R: ----- Warnings ----- R: NETW-2704 -- Nameserver 192.168.1.1 does not respond R: PKGS-7392 -- Found one or more vulnerable packages. R: NETW-2705 -- Couldn't find 2 responsive nameservers R: ----- Suggestions ----- R: NETW-2704 -- Check connection to this nameserver and make sure no outbound DNS queries are blocked (port 53 UDP and TCP). R: KRNL-6000 -- One or more sysctl values differ from the scan profile and could be tweaked R: HRDN-7222 -- Harden compilers like restricting access to root user only R: PKGS-7392 -- Update your system with apt-get update, apt-get upgrade, apt-get dist-upgrade and/or unattended-upgrades R: ACCT-9626 -- Enable sysstat to collect accounting (no results) R: MACF-6208 -- Check output of aa-status R: AUTH-9328 -- Default umask in /etc/login.defs could be more strict like 027 R: BOOT-5122 -- Set a password on GRUB bootloader to prevent altering boot configuration (e.g. boot in single user mode without password) R: LOGG-2190 -- Check what deleted files are still in use and why. R: SSH-7408 -- Consider hardening SSH configuration R: NETW-2705 -- Check your resolv.conf file and fill in a backup nameserver if possible R: STRG-1846 -- Disable drivers like firewire storage when not used, to prevent unauthorized storage or data theft R: AUTH-9262 -- Install a PAM module for password strength testing like pam_cracklib or pam_passwdqc R: PROC-3614 -- Check process listing for processes waiting for IO requests R: FILE-6310 -- To decrease the impact of a full /var file system, place /var on a separate partition R: PKGS-7420 -- Consider using a tool to automatically apply upgrades R: FINT-4350 -- Install a file integrity tool to monitor changes to critical and sensitive files R: STRG-1840 -- Disable drivers like USB storage when not used, to prevent unauthorized storage or data theft R: NETW-3032 -- Consider running ARP monitoring software (arpwatch,arpon) R: BANN-7126 -- Add a legal banner to /etc/issue, to warn unauthorized users R: TIME-3128 -- Check ntpq peers output for time source candidates R: TIME-3124 -- Check ntpq peers output for selected time source R: AUTH-9286 -- Configure maximum password age in /etc/login.defs R: PKGS-7370 -- Install debsums utility for the verification of packages with known good database. R: PKGS-7346 -- Purge old/removed packages (5 found) with aptitude purge or dpkg --purge command. This will cleanup old configuration files, cron jobs and startup scripts. R: BANN-7130 -- Add legal banner to /etc/issue.net, to warn unauthorized users R: ACCT-9630 -- Audit daemon is enabled with an empty ruleset. Disable the daemon or define rules R: LYNIS -- This release is more than 4 months old. Consider upgrading R: ACCT-9622 -- Enable process accounting R: HRDN-7230 -- Harden the system by installing at least one malware scanner, to perform periodic file system scans R: ----- Details ----- R: KRNL-6000 kernel.core_uses_pid -- kernel.core_uses_pid value is '0' prefer '1' R: SSH-7408 LogLevel -- LogLevel value is 'INFO' prefer 'VERBOSE' R: SSH-7408 TCPKeepAlive -- TCPKeepAlive value is 'YES' prefer 'NO' R: KRNL-6000 kernel.sysrq -- kernel.sysrq value is '438' prefer '0' R: SSH-7408 X11Forwarding -- X11Forwarding value is 'YES' prefer 'NO' R: KRNL-6000 net.ipv4.conf.default.accept_source_route -- net.ipv4.conf.default.accept_source_route value is '1' prefer '0' R: SSH-7408 AllowTcpForwarding -- AllowTcpForwarding value is 'YES' prefer 'NO' R: KRNL-6000 net.ipv6.conf.all.accept_redirects -- net.ipv6.conf.all.accept_redirects value is '1' prefer '0' R: KRNL-6000 net.ipv4.conf.default.accept_redirects -- net.ipv4.conf.default.accept_redirects value is '1' prefer '0' R: KRNL-6000 net.ipv4.conf.all.rp_filter -- net.ipv4.conf.all.rp_filter value is '0' prefer '1' R: KRNL-6000 net.ipv6.conf.default.accept_redirects -- net.ipv6.conf.default.accept_redirects value is '1' prefer '0' R: KRNL-6000 kernel.kptr_restrict -- kernel.kptr_restrict value is '0' prefer '2' R: SSH-7408 MaxSessions -- MaxSessions value is '10' prefer '2' R: SSH-7408 Port -- Port value is '22' prefer '' R: SSH-7408 ClientAliveCountMax -- ClientAliveCountMax value is '3' prefer '2' R: KRNL-6000 net.ipv4.conf.all.accept_redirects -- net.ipv4.conf.all.accept_redirects value is '1' prefer '0' R: KRNL-6000 net.ipv4.conf.all.log_martians -- net.ipv4.conf.all.log_martians value is '0' prefer '1' R: KRNL-6000 kernel.yama.ptrace_scope -- kernel.yama.ptrace_scope value is '0' prefer '1 2 3' R: SSH-7408 AllowAgentForwarding -- AllowAgentForwarding value is 'YES' prefer 'NO' R: KRNL-6000 net.ipv4.conf.all.send_redirects -- net.ipv4.conf.all.send_redirects value is '1' prefer '0' R: SSH-7408 Compression -- Compression value is 'YES' prefer 'NO' R: KRNL-6000 net.ipv4.conf.default.log_martians -- net.ipv4.conf.default.log_martians value is '0' prefer '1'
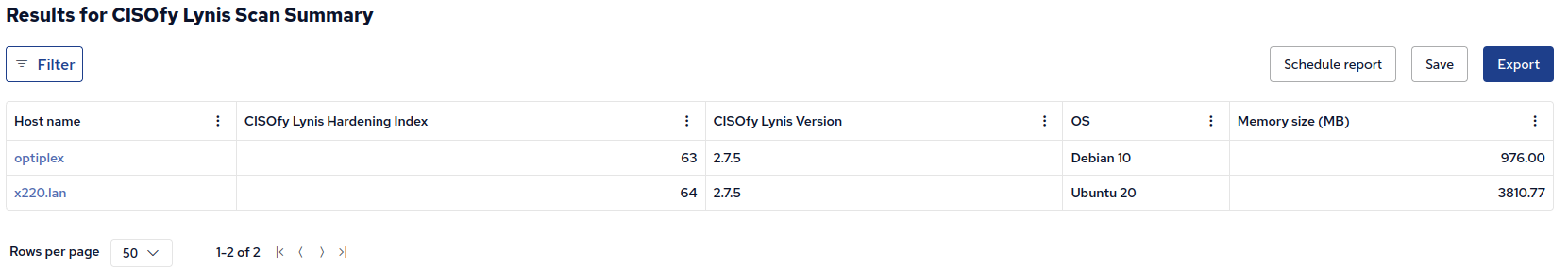
CFEngine Enterprise Reporting
Dependencies
This module has no dependencies